The Two Hidden Networks
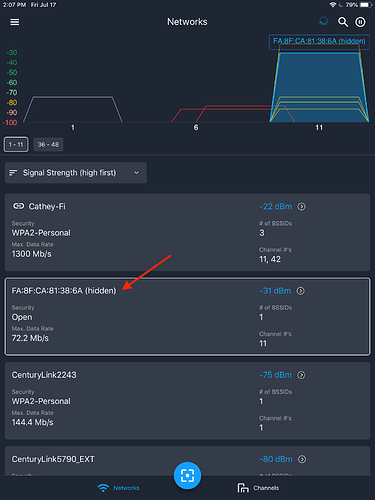
A few days ago, I decided to take complete control of my network and alias all my devices in inSSIDer so that I could monitor device utilization. To my surprise, I found two networks eerily close to me (above -64 dBm) that I didn’t recognize, both hidden and displayed as Open security.
At first, I thought they were neighboring WiFi networks but soon realized they were beaconing from inside my house. I decided that I really needed to figure out what was going on.
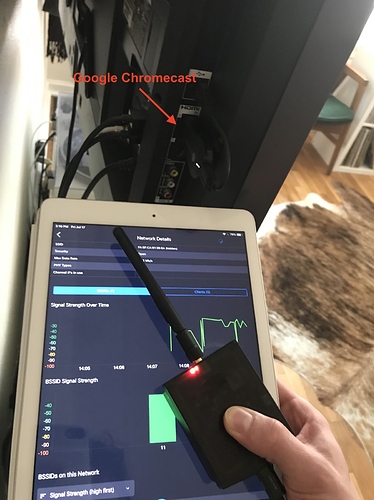
Since my laptop running inSSIDer was tethered to my display, I decided to use Wi-Spy Air and an iPad to walk around and try and find the culprit behind these networks. I started with the hidden network on channel 11 by diving into the network card and monitoring the signal strength.
My initial guess is that it was coming from an 802.11b WiFi adapter that I had plugged into a USB hub, so I lowered the Wi-Spy Air toward the hub and the signal strength dropped. That wasn’t it. I then decided to take the Wi-Spy Air outside my room and monitor the readings and the signal strength went up. I was getting closer. Eventually I was able to discover the culprit deploying the network, it was right above my regular access point and plugged into my television.
My Google Chromecast! I had no idea it was deploying an Open network and possible security vulnerability into my network. After some research, I discovered that Chromecasts will deploy this Guest mode network to allow nearby devices to cast video content without being on the WiFi network. While it’s a neat feature, I didn’t appreciate it being turned on by default. I was able to use the Google Home app and turn this feature off.
On to the next hidden network
Using the same method as above, I was able to discover the next hidden network which was curiously located in the 5 GHz band on channel 161. I already had a suspicion of the cause of this network thanks to an observant attendee in one of my recent webinars. After some research and investigation with Wi-Spy Air, I was able to indeed verify that this was deployed by my Xbox One X to allow a remote app to control it. Another interesting note is that Air Viewer showed this network as WEP security, which is a little better than Open but still easily crackable.
To be safe, I was able to turn this network off from the Xbox settings under Devices & streaming > Device connections by selecting Don’t allow the Xbox app to connect.
Once this was done, I fired inSSIDer back up and lo-and-behold I had a nicely cleaned up WiFi environment. The only network in my proximity was my own, secure network.
Now about that overlapping network on channel 8…